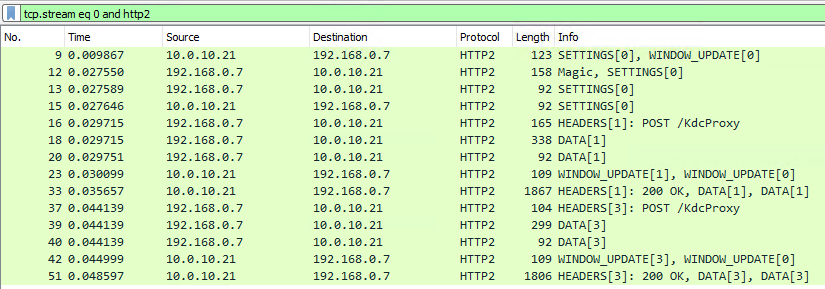
Windows Hello for Business cloud trust is the latest addition to deployment methods that can be used for Windows Hello for Business.
Windows Hello for Business cloud trust Windows Hello for Business is Microsofts passwordless logon solution that uses an asymmetric key pair for authentication instead of using username and password. The private key is securely stored in the Trusted Platform Module (TPM), preventing the private key from getting leaked. All the technical complexity of the logon process is completely transparent to the user, she only has to unlock the credentials stored in the TPM using either a PIN or some kind biometrics.
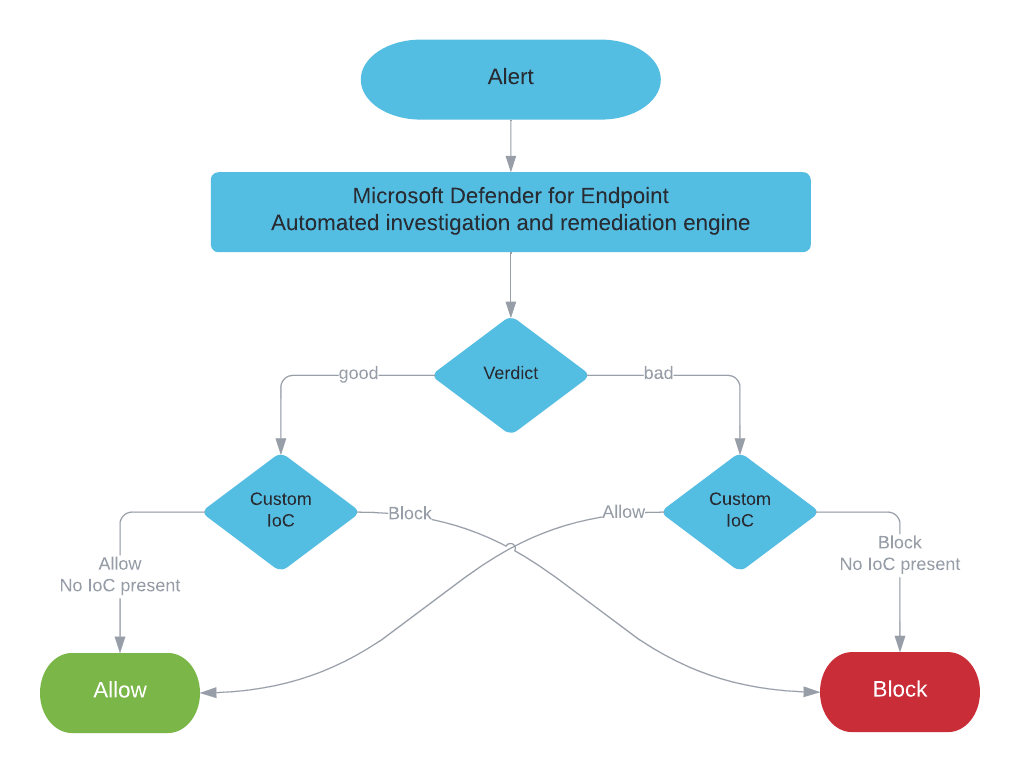
Since Microsoft Defender for Endpoint is a suite of products, rather than just one single piece of software, there are various places where you can create exclusions for different features. Also, there are integrations in other products, that result in possible side effects when enabling certain settings.
Most of these products have separate documentations, there is no single documentation page that contains all the information about exclusions available in Microsoft Defender for Endpoint.
Am Donnerstag, den 12. Mai, werde ich bei der Cloud Workplace Meetup sprechen. Das Thema meines Vortrags ist “Use external threat intelligence in Microsoft Defender for Endpoint”.
Ausblick Mit Microsoft Defender Tamper Protection bietet Microsoft einen essentiellen Baustein für die Absicherung der Antivirenlösung auf Endpoints, Server wir Clients zugleich. Die Funktion verhindert die Abschaltung der Schutzkomponenten und erschwert es Angreifern Ihren Payload unbemerkt zu starten.
In dieser Session erörtert Fabian Bader welche Bereiche der Antiviren Software durch diesen Schutz abgedeckt sind und zeigt auf welche Konfigurationsänderungen weiterhin möglich sind.
Am Donnerstag, den 28. April, werde ich bei der Microsoft Cloud Security User Group sprechen. Das Thema meines Vortrags ist “Use external threat intelligence in Microsoft Defender for Endpoint”.
Ausblick Extend alarming and protection capabilities of Microsoft Defender for Endpoint using external data sources. In this showcase Fabian Bader will demonstrate how easy you can tap into open source threat intelligence using the Feodo Tracker project and use it to protect your endpoints.
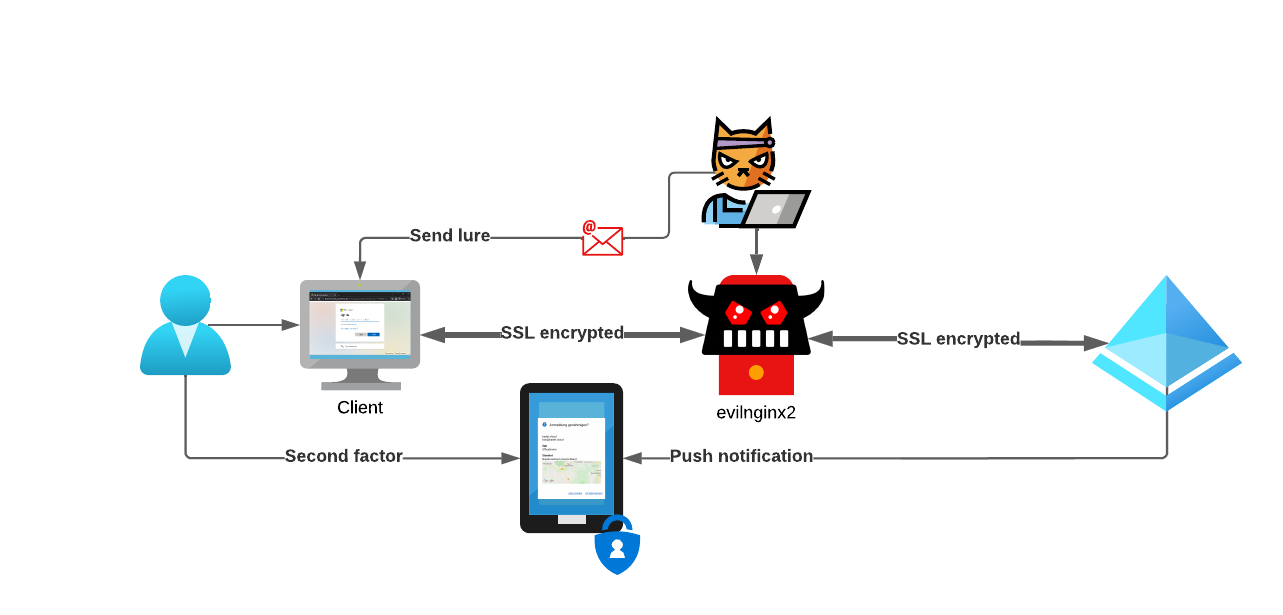
Microsoft offers a great variety of options to use as your primary authentication method, when signing-in with your Entra ID (Azure AD) identity using a browser.
Username and Password Phonenumber and SMS Username and Passwordless phone sign-in Certificate-based authentication Windows Hello for Business FIDO2 security keys Using conditional access you can further protect the accounts, enforcing the need for a second factor, device compliance, location based restrictions and many more configuration options.
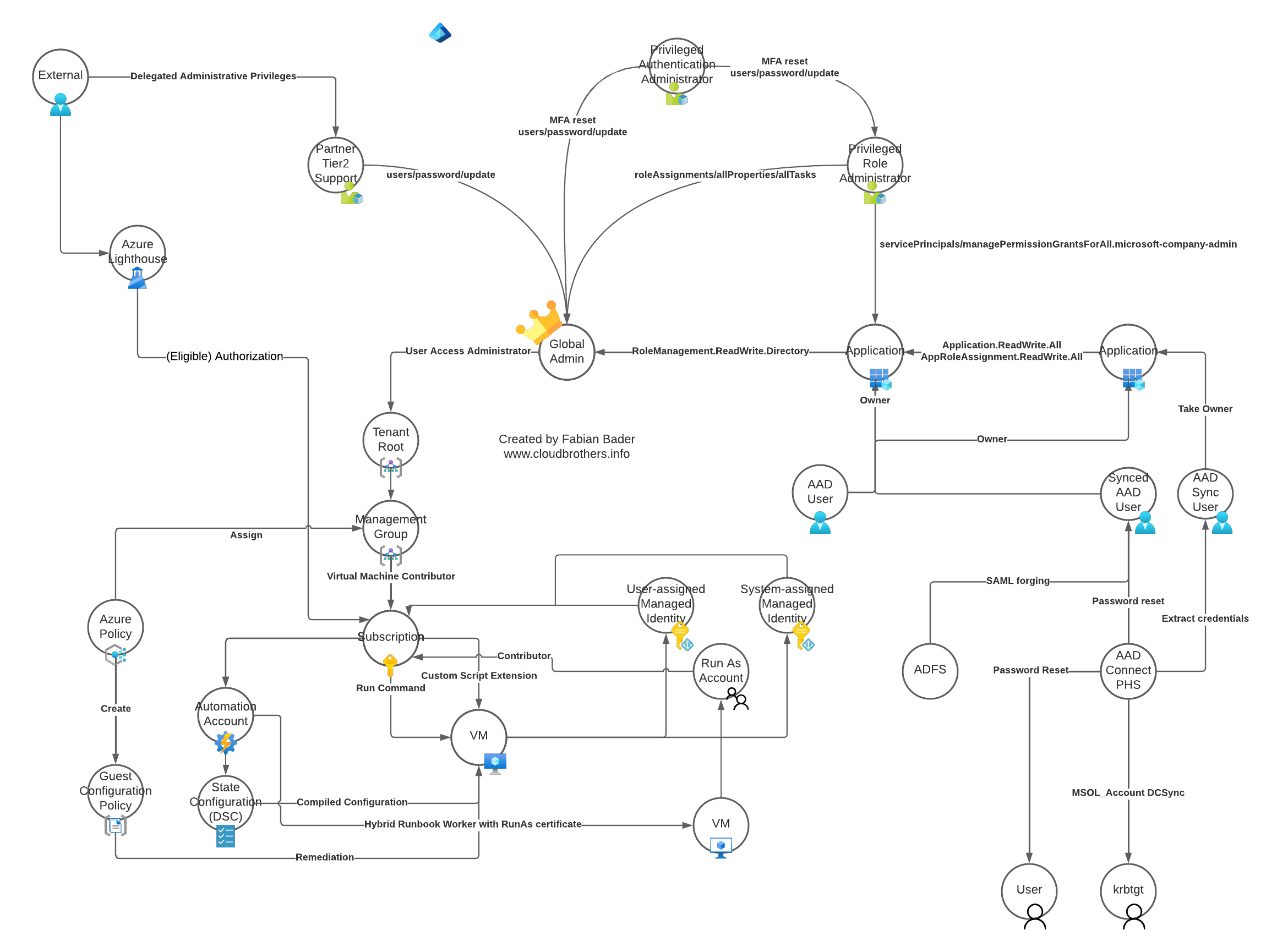
Creating and maintaining a secure environment is hard. And with every technology or product added to your environment it gets more complicated. Microsoft Azure as a cloud environment is no exception to this rule and with the many services and features that get added every year it just gets more complicated even if you did not change a thing. Because keeping your IT assets secure is important as you move to the cloud, it is important to know which bad practices to avoid and which attack scenarios are out there.