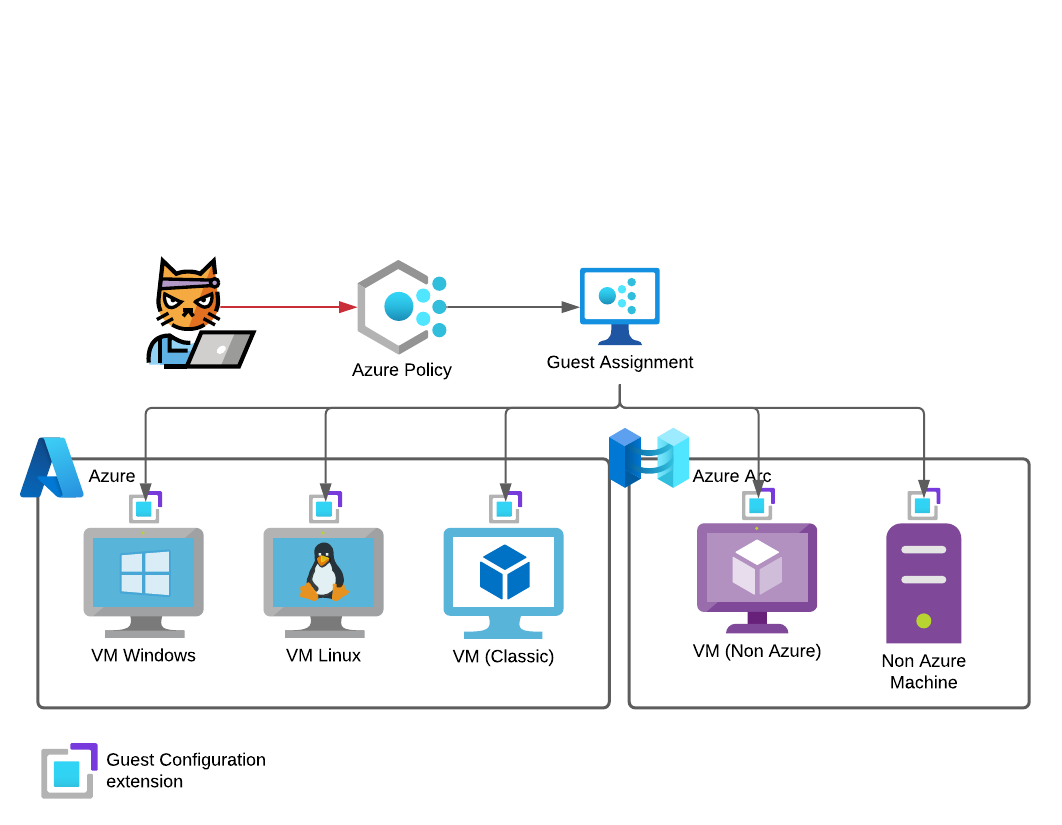
Azure Policy enables administrators to define, enforce and remediate configuration standards on Azure resources and even on non Azure assets using Azure Arc. One key feature, that was released in 2021, is the guest configuration feature of Azure Policy.
Basically, this is the new implementation of Azure Automation State Configuration or as it is widely known PowerShell Desired State Configuration (DSC). Microsoft states this on the product page very clearly.
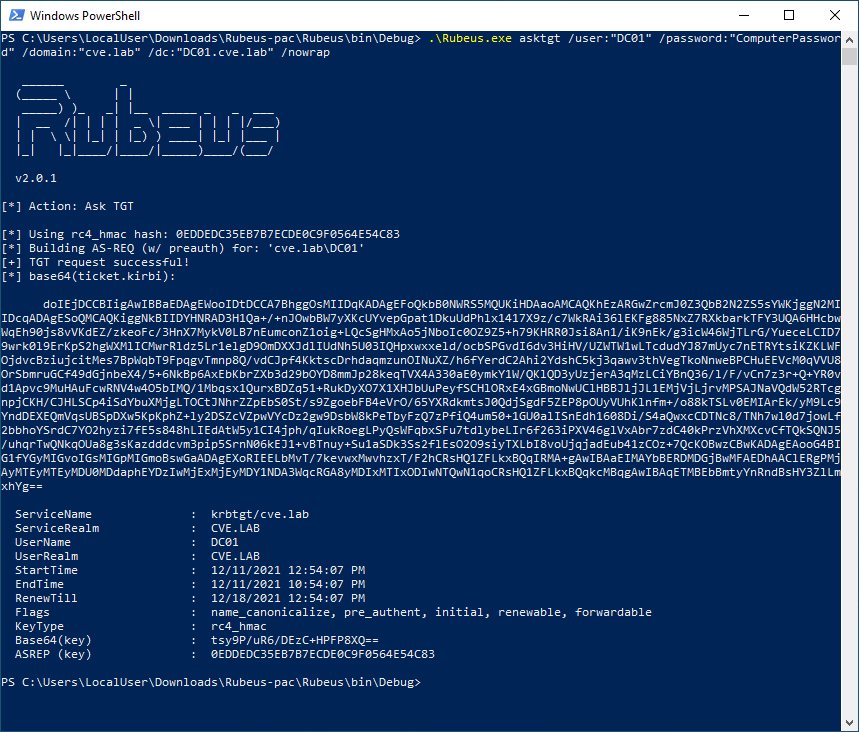
When Microsoft released the November 2021 patches, the following CVEs caught the eye of many security professionals because they allow impersonation of a domain controller in an Active Directory environment.
CVE-2021-42278 - KB5008102 Active Directory Security Accounts Manager hardening changes CVE-2021-42278 addresses a security bypass vulnerability that allows potential attackers to impersonate a domain controller using computer account sAMAccountName spoofing.
CVE-2021-42287 KB5008380 Authentication updates CVE-2021-42287 addresses a security bypass vulnerability that affects the Kerberos Privilege Attribute Certificate (PAC) and allows potential attackers to impersonate domain controllers.
On Tuesday, December 14th, I will be speaking at the Trust in Tech Cologne virtual meetup. The topic of my talk is “Protect your endpoint from known C2 Feodo servers”.
Abstract As Emotet is back from the dead the cyber security landscape is getting even more dangerous as before. Thankfully open projects like Feodo Tracker provide information about active C2 servers. Learn how you can utilize the provided Indicators of Compromise, Microsoft Defender for Endpoint and Azure Automation to add an additional layer of security for your endpoints.
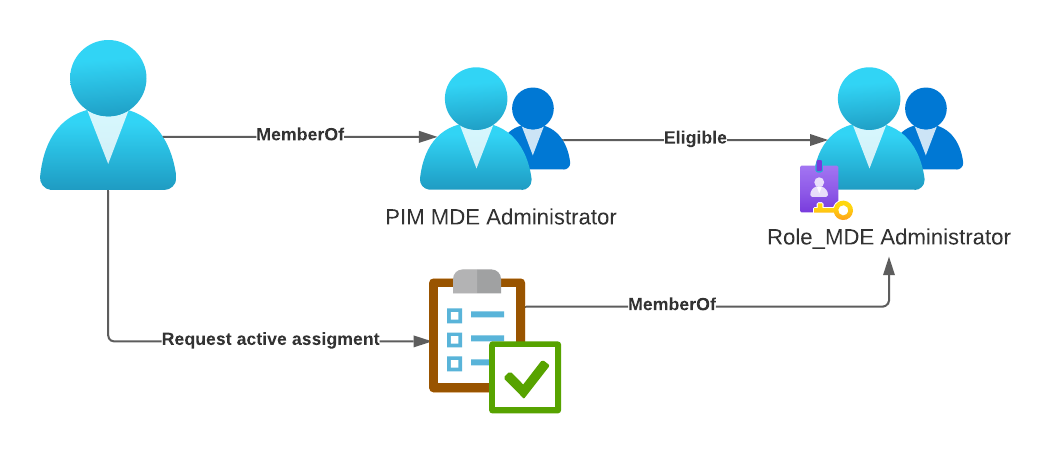
For a long time assigning multiple Entra ID (Azure AD) roles to a user was a tedious task in not done via a script. Every role assignment had to be made separately. This also made it hard to change role assignments for a group of people.
That all changed when Microsoft introduced Entra ID (Azure AD) role-assignable groups. It is now possible to assign multiple roles to one group and add the users to this group.
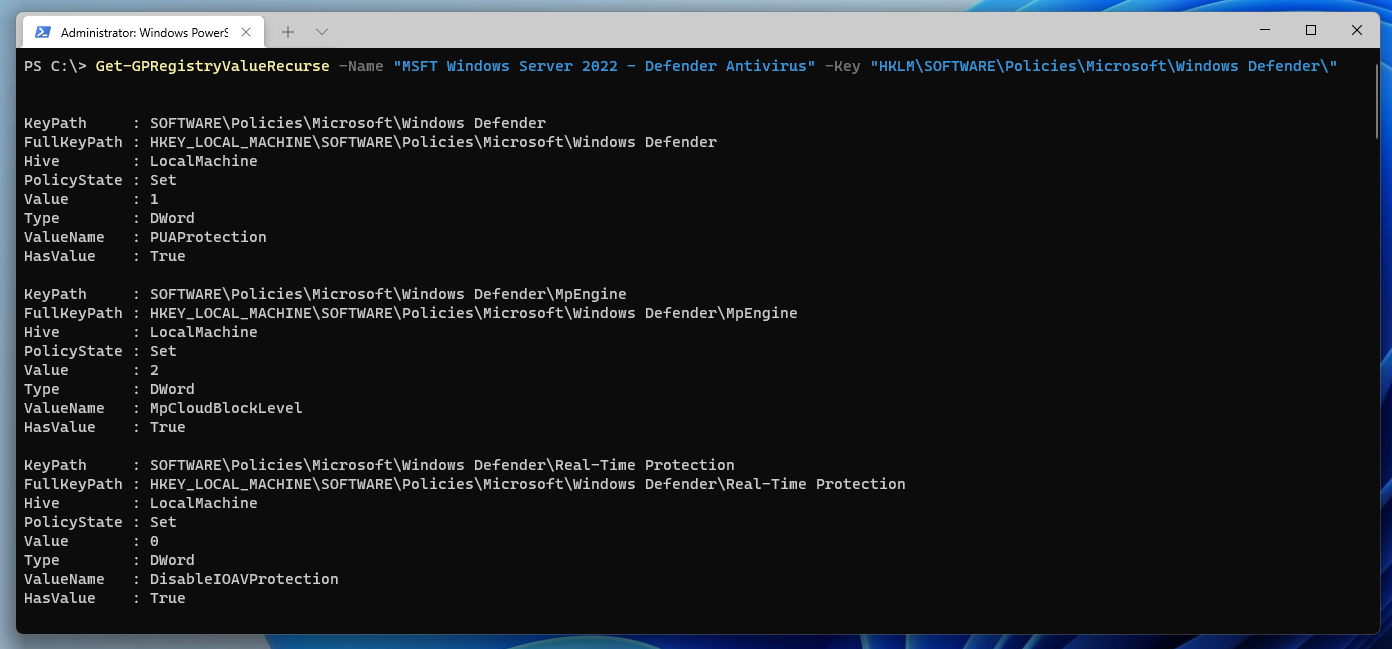
Despite Intune, DSC and Azure AD; group policies are still a widely used method to manage Windows clients and servers in many companies. However, the MMC is not really suitable for managing several hundred GPOs. But that’s what PowerShell is designed for.
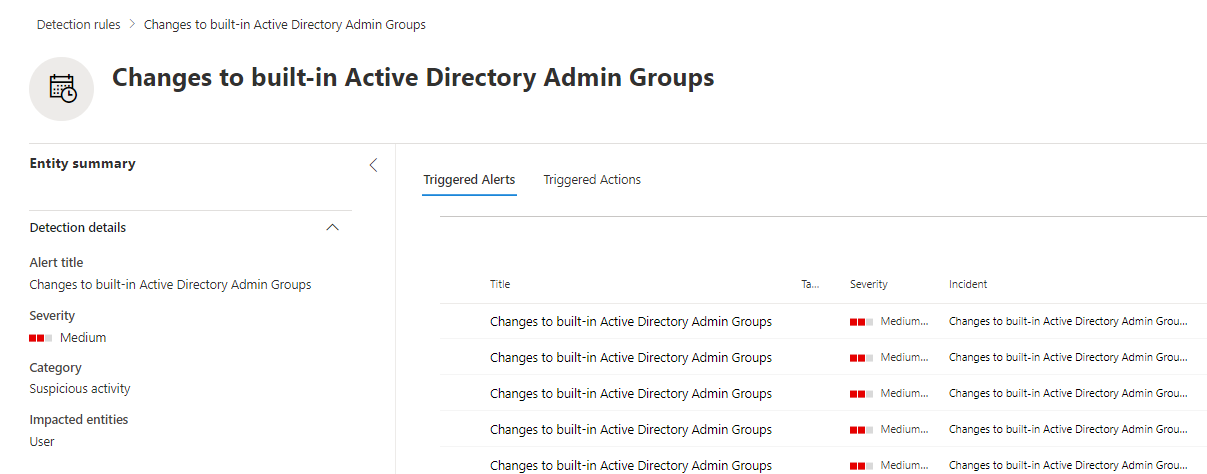
Microsoft Defender for Identity is a very powerful tool when it comes to track changes to users and groups in your on-prem Active Directory. When used in combination of the advanced hunting capabilities available in the Microsoft 365 Defender portal and custom detection rules you can very easily automate the change tracking.
If you protect any on-prem Active Directory, you should be aware to changes to any privileged groups. Microsoft itself list a few of them in their documentation on Active Directory Domain Services and in the Defender for Identity documentation adds additional ones.